Entra: Securing Teams Phones using Conditional Access - The Device Code Flow Dilemma
- Will Francillette

- Mar 16
- 5 min read
Updated: Mar 17

This blog is a bit different from usual. I worked on a project to secure device code flow in an environment where Microsoft Teams Phones and Rooms are used. I used Conditional Access policies to limit the use of this authN method but encountered many difficulties. Device code flow is a high-risk authentication flow that might be used as part of a phishing attack or to access corporate resources on unmanaged devices. The phones are all identical, Entra registered and managed via Intune. I've used as reference Microsoft documentation but wasn't able to implement most of the restrictions I initially planned.
I thought of documenting these outcomes so that it may help others and keep track on all this issues.
Let's get started!
Table of Contents
Overview
In our scenario, I want to block device code flow for most user in the organisation.
Teams phones and rooms are found across the organisation and users are using remote registration and sign-ins which use Device Code Flow to complete the process. It is a convenient way and users don't need to enter their credentials on the phone screens.
Teams phones don't support all scenarios covered by conditional access so I used this documentation as a reference: Supported Conditional Access and Intune device compliance policies for Microsoft Teams Rooms - Microsoft Teams | Microsoft Learn
Restriction 1: enable Device Code Flow for a restricted set of users
I used a block all approach and exclude those sanctioned users from the policy.

✅This worked well, no issue with assignments.
Restriction 2: enable Device Code Flow on specific location only
Same approach here, we blocked Device Code Flow from anywhere except specific locations.

✅This worked as well
Restriction 3: enable Device Code Flow from specific application only.
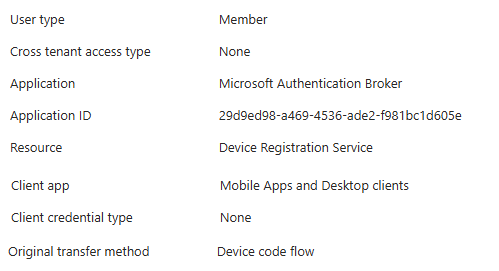
Here to restrict the attack landscape I wanted to only allow the minimum application required for those phones to work - My policy blocks all apps except those mentioned in the below screenshot

❌Failure 1 - The authentication process is transferred to the Microsoft Authentication Broker which couldn't be excluded
Restriction 4: enable Device Code Flow for selected OS only
Because all my phones are Android, I wanted to only allow the authentication on this operating system. So I tried targeting all device platforms except android

❌Failure 2 - This didn't work because despite being initiated from Android the verification is performed on Windows (or what ever OS you are using). The logs were still showing Android even though the device information was the laptop used for the verification and not the phone it was initiated.
The below screenshot was taken from the sign in logs - we can see that it was Entra joined, and managed but the operating system was showing Android despite being a Windows laptop.

When I looked up the device ID in the Entra portal I could clearly see the inconsistency in the logs:

Restriction 5: enable Device Code Flow for specific devices
My next thought was to restrict device code flow on those phones only especially that they are all the same brand and model. I was planning to use filter for devices and which is supposed to be supported

❌Failure 3 - It tried everything 😭 ... All my phones are enrolled and managed via Intune, they all have same manufacturer and model number and can see the information in the device page in Intune. I tried using an exclude filter ie block all apps for Device Code Flow except my phones - I checked the filter for devices documentation to ensure my filter was sound and supported - I tried to be as basic as possible using the model or manufacturer attribute but nothing worked.

The Microsoft Teams phones documentation also show similar examples but no luck unfortunately... My devices were still being targeted and never excluded from the policy. The resource for troubleshooting are very limited, I would have loved to be able to see the result of a filter for device in the sign in logs when a conditional access is used. I can only guess that the issue is due to the confusion between the device that initiate the authentication and the device that verifies the code in the logs as you could see the mixed up with device platform in restriction 4.
Bonus - Troubleshooting: SIF and TOU
During my troubleshooting/research, I came across a possible issue when Term of Use and Sign-In Frequency applies on those devices.

❌Failure 4 - I was hoping this was the cause of all my problems so disabled TOU but unfortunately it was a fail as well
Conclusion
This has been a very frustrating experience especially with the filter for devices - I wish we could at least see if a value was retrieved for the specified attribute and find more information to try to understand where the flow failed. I am all for blocking Device Code Flow as default but there are some use cases like Teams phones/rooms ( I also heard of AKS and kubelogin authentication) that need to be covered and allowed in restricted circumstances.
I hope this will help and if you have any insights don't hesitate to DM me on LinkedIn
Thanks for reading!
References
About William Francillette:

I am DevSecOps Lead and Solution Architect at Threatscape specialised in M365 and Azure security offering.
I love learning, blogging and coding. My interests are very diverse and span across architecture, security, cloud engineering, automation, DevOps and PowerShell.
I own as of today 17x (and counting) Microsoft certifications and have worked in IT across multiple and diverse industries for over 15 years.







Comments